3 min read
MAXIMIZING CYBER INSURANCE: 5 BENEFITS OF PARTNERING WITH AN MSSP
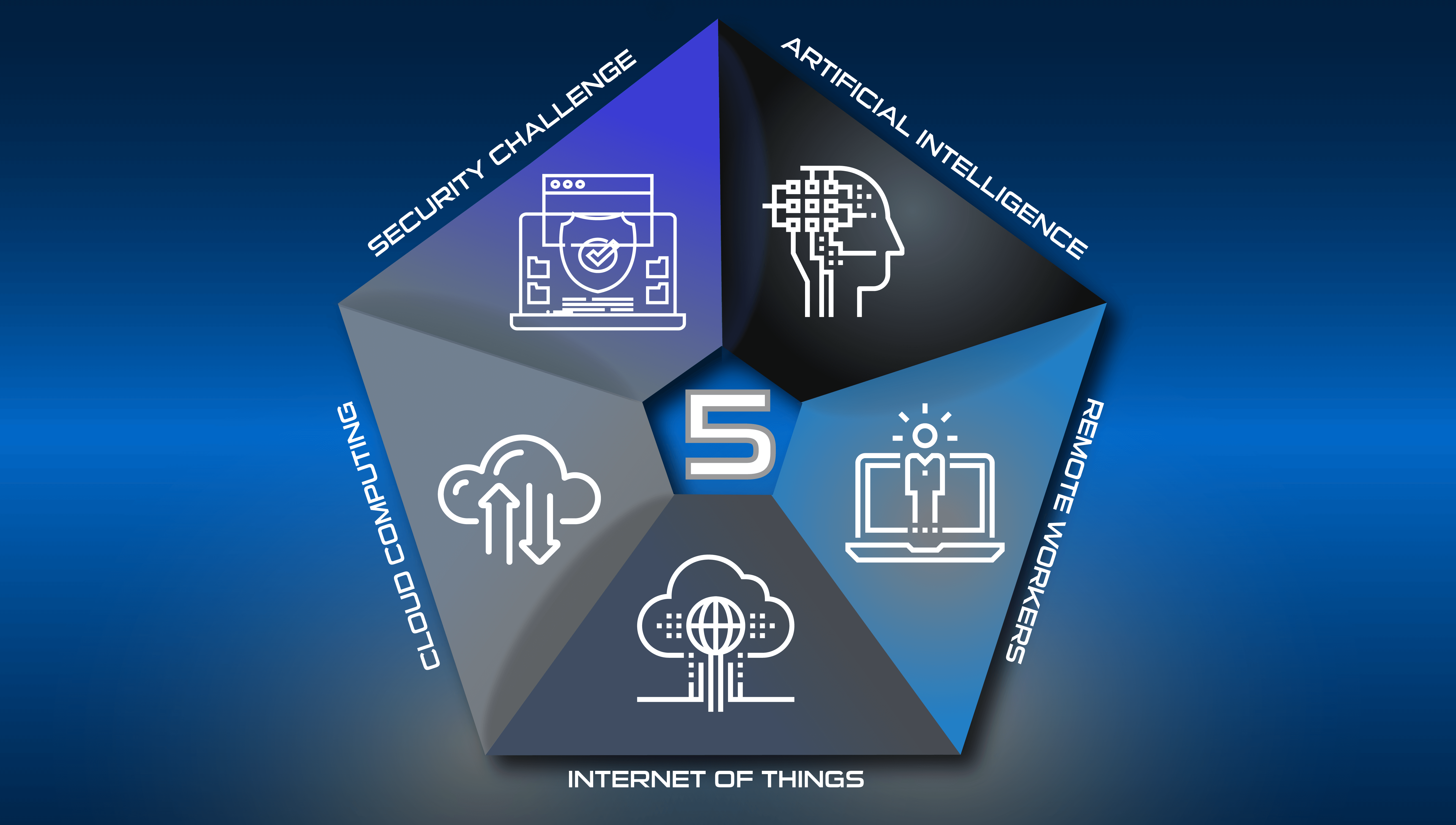
Cyber insurance has emerged as a crucial component of risk management, offering financial protection against the potentially devastating consequences of cyberattacks. However, obtaining and maintaining effective cyber insurance coverage can be...
Read More