How To Prevent Ransomware
In 2020, there were approximately 304 million ransomware attacks worldwide. These types of attacks are an ongoing growing threat for business owners....
5 min read
 Joseph Ugalde
:
Nov 5, 2021 12:26:51 PM
Joseph Ugalde
:
Nov 5, 2021 12:26:51 PM

Cybercrime is having a truly major impact on the global economy, a new report has claimed. According to McAfee, in 2018, cybercrime cost the global economy more than $600 Billion. Today, this has escalated to a 1 trillion pull on the global economy, an approximation to 1% of the worldwide GDP.
Having a firewall can make a big difference in protecting your devices from security breaches. Firewalls help secure networks and devices from many security risks, like those from unauthorized access from cybercriminals.
In this article, we'll cover everything you need to know about network firewall security, along with how to avoid common cybersecurity issues to guard your business and its information against malicious attacks.
British police said that the first six weeks into the COVID-19 pandemic, phishing scam reports increased as high as 400%. Google revealed that 18 million malware and phishing emails are blocked every day related to the COVID-19 pandemic.
If you aren't concerned yet, take a look at the following statistics to understand the severity of the problem:
Need help protecting your company from malicious attacks like ransomware and other types of cyberattacks? Systems X has a variety of services to help you! Contact our professionals today!
Cybercriminals use hacking, phishing, and identity theft to steal money from you. However, cybercriminals are now more sophisticated than in the past. Today, they want your personal information, like name, DOB, Gender, IP address, Age, Location, profile pictures, bio descriptions, and more.
The types of organizations and objects hackers target the most are:
Having an updated firewall security measure is among the essential cyber protection tools that companies -- small or big -- use to prevent data breaches and hacking. If you want to guard your organization against unwanted cybercriminals, it's vital to keep your firewall up-to-date with the latest firmware.
Although no protection is perfect, some protection is better than having no protection at all. It's crucial to make it harder for hackers to enter your organization and breaking havoc. A firewall is one of the first lines of defense to safeguard your information.
Related: 3 Types of Software Every Manufacturer Should Use
According to IBM, the US has the world's highest data breach costs, with the average attack costing $8.6 million. If you live in the US, you should be concerned about updating all your systems with the latest patches.
Investing time and resources in a reliable Network firewall security system can filter out incoming traffic to prevent downloading malicious files and block attackers from accessing sensitive systems. That's why you should get a reliable MSP like Systems X to help you with your cybersecurity needs.
A firewall's primary function is to work as a gatekeeper. A Network Firewall Security can control access to your organization's network, hence protecting its information.
It monitors all attempts to gain access to your operating system, blocks unwanted traffic or suspicious sources, and filters the communications between connected networks.
Here are 11 things a Network Firewall Security can protect you against:
Related: 5 Common Cyber Threats to Watch Out For
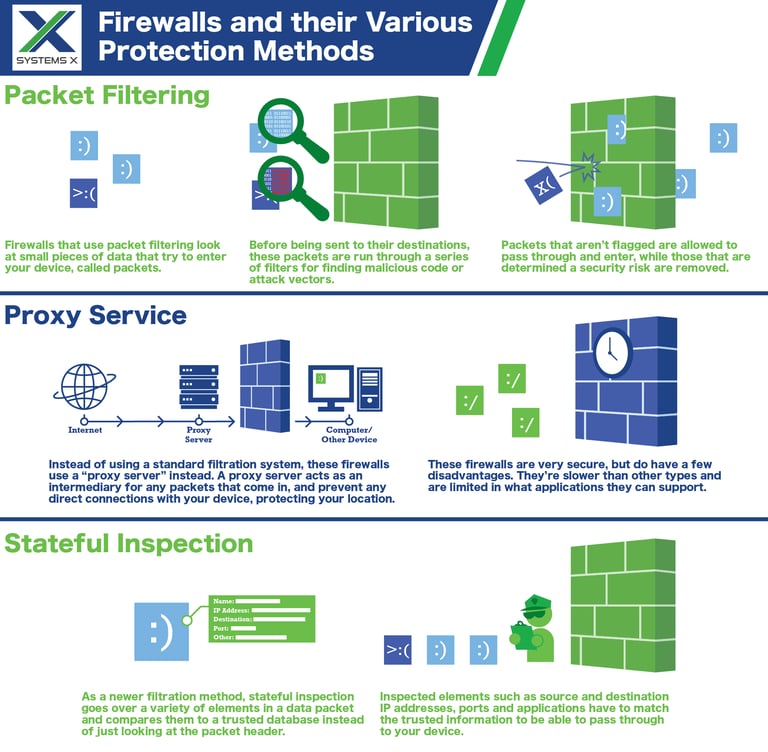
A firewall works by acting as a protective barrier between the user and the Internet. A firewall has a configuration that only welcomes those incoming connections that are familiar to it. It does this by allowing or blocking suspicious activity and regularly monitoring data coming in and out. The data transferred is known as "packets," which may or may not contain malicious codes to damage your system.
Only trusted IP addresses or sources are allowed in. IP addresses are necessary because they identify a computer or origin, just like your postal address recognizes where you live.
Hackers bombard your network during busy days or peak holiday seasons with malware, spam, virus, and other malicious intent.
At this time, your firewall applies a specific set of rules on the incoming and outgoing network traffic to examine whether they align with those rules or not.
There are many types of firewalls used in modern security structures. Unfortunately, many attackers know how to break a firewall—and some insider threats can bypass them entirely. Nonetheless, having a firewall, it's essential to keep your system as safe as possible.
Packet filters help to prevent undesired traffic from entering the network. As mentioned already, they apply a set of network firewall security rules to determine whether to allow or deny access. The firewall checks "packets" passing through the router.
The checked information includes destination and originating IP address, packet type, and other surface-level details. These attributes determine if the packet or inkling traffic must be given access through the firewall or not.
The proxy service firewall system helps to protect the network security by filtering messages at the application layer. It functions as the only entry point to and exit point from the network. Also known as a gateway firewall or proxy firewall, it is more secure in using deep packet inspection technology to analyze incoming traffic and other characteristics, such as the HTTP request string.
The multi-layer inspection firewall cleans traffic based on port protocol and state, along with administrator-defined rules. It involves using data from prior connections and packets from the same connection. Compared with other firewalls, it can provide a higher protection level. Stateful inspections and firewalls that use this technology reject any traffic between trusted and untrusted interfaces.
A NAT or Network Address Translation firewall can deny unsolicited communications, and it only accepts web traffic if a device requests it.
Devices connected to your router can communicate with the Internet through one external IP address. Your router acts as a middleman between devices on your local network and the Internet, and all internal IP addresses remain hidden when you go online.
A virtual firewall is a tool used in a cloud-based system, both private and public. This type of firewall assesses and manages internet traffic over both physical and virtual networks.
Related: Does Your Business Need Technology Consulting?
You do! If you use the Internet, it's wise to have a firewall in place. They provide the first line of defense to help protect your computer and your personal information from cyber threats, which are rapidly evolving and spreading.
Safe habits you can implement today to surf the web safely are:
Picking the ideal firewall starts with understanding the structure and roles of private network protection. It's also crucial to understand the different firewalls and policies that are most effective for your company.
Whichever firewalls you choose to have, keep in mind that a misconfigured firewall can, in some ways, be more dangerous than no firewall at all because it gives the false impression of protection while providing little to no protection.
Looking for a team of reliable professionals who can help you meet your cybersecurity needs? Contact Systems X to get expert assistance today!

In 2020, there were approximately 304 million ransomware attacks worldwide. These types of attacks are an ongoing growing threat for business owners....

Keeping your business safe isn’t usually a single step. It’s a series of vital steps designed to build a barricade around you and your most vital...

Email communication is now what makes the world go ‘round. While the pandemic has exacerbated the need for online communication channels, email has...