The Complete Guide to Email Security
Email communication is now what makes the world go ‘round. While the pandemic has exacerbated the need for online communication channels, email has...

With everyone growing increasingly reliant on technology and the digital realm gaining so much power over the physical realm, the concept of cybersecurity has never been more relevant than it is today. From DDoS attacks to phishing scams and other common cyber threats, businesses and individuals alike have more to worry about than ever when keeping their private data and personal information safe.
The industry experts at Systems X are here to provide you with quality cybersecurity services and information articles you can use to gain a solid education on these potential threats and help ensure you’re protected from the various dangers of the cybercriminal world. Please continue reading to find out everything you’ll need to know about the threat of URL phishing and the ways you can prevent it from wreaking havoc in your life today.
Have a question about one of our services, the industries we work with, or something else? Connect with us here.
In short, URL phishing is a method utilized by hackers to “fish” for your private information within the digital world. The practice typically involves a hacker sending victims a fake but realistic-looking login page for a familiar or commonly used website to trick the victim into typing their username and password. Once the hacker acquires this information, they then have access to the victim’s real account. From there, the hacker may attempt to steal the victim’s identity, read private emails, lock them out of accounts, and even move money out of their bank account.
RELATED: Network Firewall Security: How You Can Make Full Use Of It
Phishing websites will typically reach out to prospective victims using three distinct methods, including:
Say a woman tries to pay her phone bill online and types in “FastMobile,” before clicking the first link that pops up. However, she doesn’t notice that the first link is actually a paid Google Ad that leads to the phishing site “FastMobille.com,” with an extra L. She pays her bill but then notices several fraudulent charges on her credit card.
Say a man gets an urgent email from his “bank” warning of suspicious activity on his account. He’ll click the link and go to a fake site to change his password. Now hackers have all the information they need to get into his actual bank account and empty it.
Say a woman gets an email from the CDC warning about a local COVID-19 outbreak. She follows the link to provide contact and medical information in exchange for regular updates. Now, hackers using the fake site have access to information that may allow them to perform medical identity theft.
It’s essential to take steps to identify and protect yourself against potential phishing attacks. Here are several steps you can follow to identify phishing URLs:
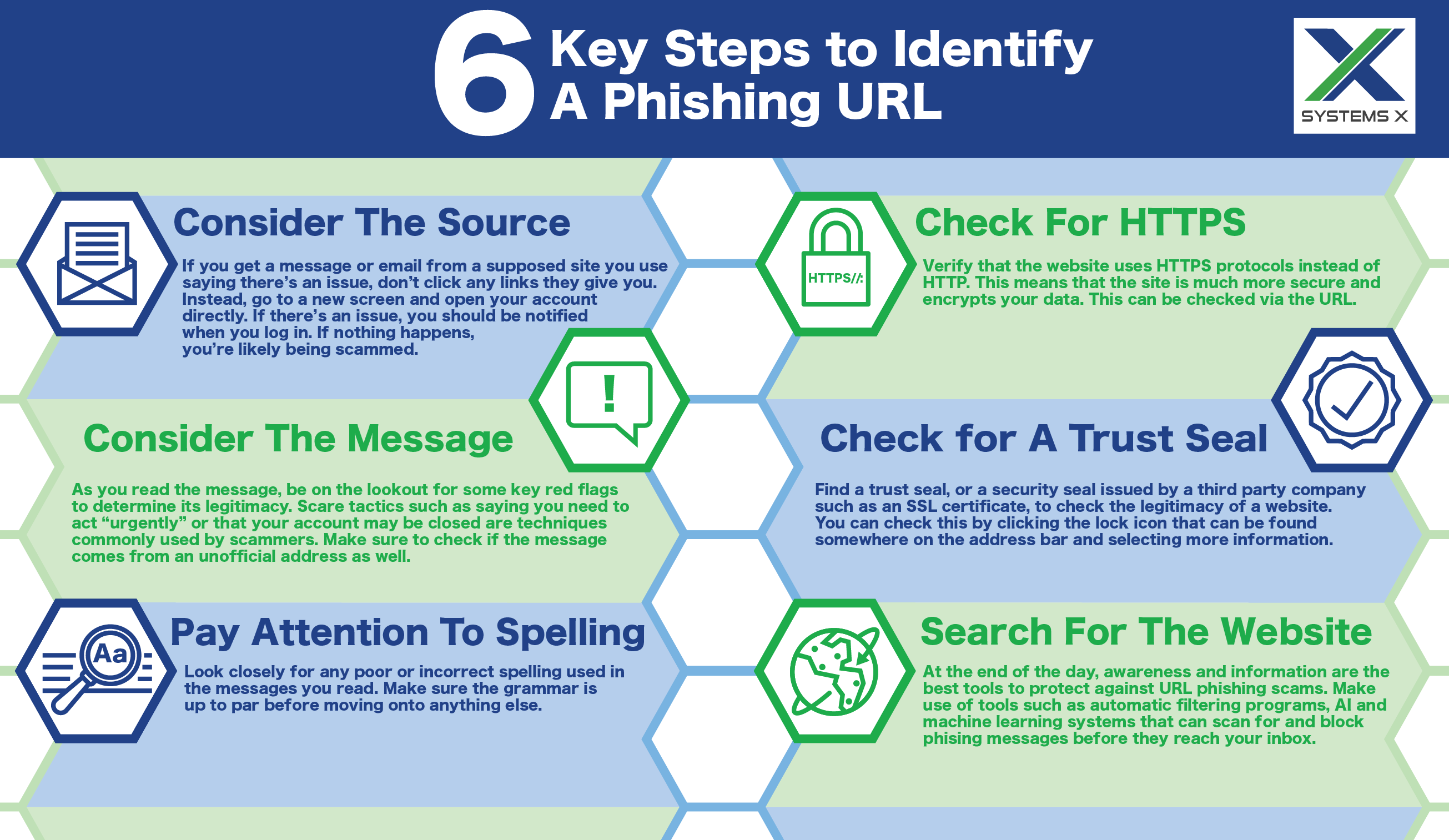
If you get a text message or email directing you to a site you commonly do business with, saying there’s an issue, don’t click the link, especially if the URL looks suspicious. Go to a new screen and open your account directly. If there’s an issue, you should be notified when you log on and can fix it from there. If nothing happens, you’ll know you are likely being scammed.
Also, be on the lookout for strange country domains (.uk, or .io, for example) or long strings of symbols or text, especially if it’s written in another language or uses a different alphabet. Always be sure to read through the URL of the site diligently to help identify potential red flags.
Ask yourself if the message seems legitimate, and be on the lookout for some key red flags. For example, if the message asks you to act “urgently” or warns that an account of yours may be closed, it’s probably a scam. This is a scare tactic fraudsters will use to trick people into acting without thinking.
Also, be on the lookout if the message comes from an unofficial address or one that contains lousy grammar, incorrect spelling, or a generic message like “Dear Customer.” Additionally, never trust a message asking you to provide or verify confidential information.
RELATED: Everything You Need To Know About Spear Phishing
As stated briefly above, pay close attention to incorrect spelling and bad grammar in any message you receive or sites you may be sent to. It’s usually easy to tell a fake from an authentic site if you look closely enough. Unleash your inner proofreader before deciding to trust anything.
Ensure that the website uses HTTPS protocols instead of HTTP, which means the site is much more secure and encrypts your data. You can determine this by clicking on the site’s URL for more information.
RELATED: Date Breaches Are Increasing The Need For Cyber Liability Insurance
Check to ensure the website’s legitimacy by looking for a Trust Seal or security seal issued by a third party company, such as a Secure Sockets Layer (SSL) certificate. These can be checked by clicking the little lock symbol that may be present to the right of the address bar and selecting “more information.”
In the end, awareness and information are the best tools in a person or business’s arsenal to protect against URL phishing scams. Still, there are several other methods you can also rely on to help better ensure your data’s safety. Please make use of various technological tools and services, such as automatic URL filtering programs, artificial intelligence, and machine learning systems that can scan and block spam and URL phishing messages before they even reach your inbox.
It’s essential to keep yourself protected from potential hacking scams and URL phishing attacks from those who want to take advantage of you. Please keep the above information in mind to safely avoid the sly tactics of savvy cybercriminals in the online world. And if you’d like more information or assistance in ensuring your online protection by utilizing effective cybersecurity solutions, please get in touch with the trusted industry experts at Systems X today.
Systems X connects you with modern cybersecurity solutions. Learn more about our services here.

Email communication is now what makes the world go ‘round. While the pandemic has exacerbated the need for online communication channels, email has...

Cybercrime is having a truly major impact on the global economy, a new report has claimed. According to McAfee, in 2018, cybercrime cost the global...

Keeping your business safe isn’t usually a single step. It’s a series of vital steps designed to build a barricade around you and your most vital...